Secret sprawl | First encounter
As a student i always would day dream about working on real life projects. Always wondering what technologies people used, how efficient and exciting it would be to see everything in action. Life's not rainbows and flowers, so is the workforce.
Objectives are not defined by technology only. Business requirements are more important to stakeholders and especially those who work on low cost projects.
Security becomes a luxury that you implement in your free time.
With a release every two weeks, security was not a priority and explaining secrets management to your boss, is exhausting.
A secure product requires investing money in something that doesn't pay back. You don't gain money by saying i have a secure product. You are required to have a secure product by default.
Nonetheless, I try to keep my security knowledge fresh, and that introduced my to devSecOps. Security as code in an automated environment. An interesting field with a set of new challenges that saw the limelight with the rapid shift to microservices.
 I never knew how big and impactful secret sprawl is until i worked in a Tech company. Having passwords, Api keys, database credentials and certificates spread all over the infrastructure in plain text was a real mess. Microservices had to establish a machine identity, think of it like an ID. They represent independent entities working together in a decentralized environment. Therefore they had to provide proof of who they are. As a result, they are stuffed with a bunch of sensitive data that needs to be protected and delivered in a secure manner.
I never knew how big and impactful secret sprawl is until i worked in a Tech company. Having passwords, Api keys, database credentials and certificates spread all over the infrastructure in plain text was a real mess. Microservices had to establish a machine identity, think of it like an ID. They represent independent entities working together in a decentralized environment. Therefore they had to provide proof of who they are. As a result, they are stuffed with a bunch of sensitive data that needs to be protected and delivered in a secure manner.My job consisted of protecting these sensitive information and to provide visibility of who did what and when. I am not going to explain the whole infrastructure for the sake of the company's privacy. Even though i don't like the concept of security by obscurity, Nonetheless, this is not my call to make.
At first i thought finding the right secret management tool was enough to mitigate this problem. I did find the perfect software for the job. Hashcorp's Vault is a leading product written in GoLang, that is referred to as the Swiss army knife of secret management. And it's really cool! It uses Shamir's secret sharing Algorithm to seal and unseal itself. Think of it as a missile launcher, that needs multiple keys, in the hands of high security clearance dudes to work.
It can access databases on your behalf and create temporary unique credentials for your applications to use. Allows you to encrypt, and decrypt data in transit, stores sensitive information, encrypted in its backend, lets you define RBAC policies and a bunch of other functionalities.
Getting it fired up and running was not a big deal, the problem i faced was integrating this solution with our own infrastructure.
Here i faced a mountain of technologies that i needed to learn to have a proof of concept.
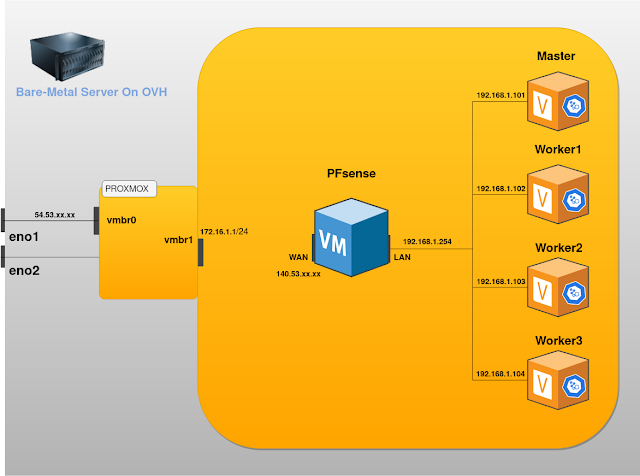
I had to learn how to design microservices which i needed to run in docker containers on top of a kubernetes cluster, that is being deployed in a cloud environment.
On top of that, as you progress you become aware that security is not about finding the right tool. The more complex the system, the bigger the attack surface.
I never worked on microservices nor docker environments before joining the company as an intern a year ago and i had to start right from hello-image to running a kubernetes cluster just to have my own setup to test vault features.
Even though it took a big chunk of my health and time to be able to keep this pace, i am really grateful being surrounded by awesome people who are willing to give me a lot of their time and who appreciate the beauty of software design.

good job !
ReplyDelete